Set up
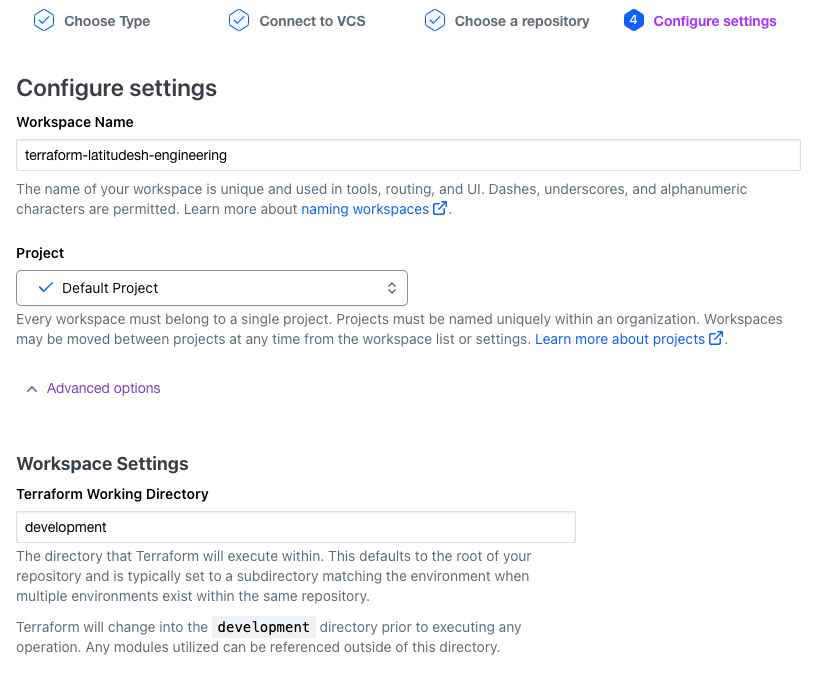
After signing up for Terraform Cloud, set up your workspace. We recommend using a Git repository. We use GitHub, but Terraform Cloud also allows GitLab, Bitbucket and Azure DevOps to be connected. Create one directory on your git repo and one workspace in Terraform Cloud for each of your Latitude.sh projects. So, if like us, you have a Development and a _Production _ project on your Latitude.sh account that you want to manage with Terraform, this is what the root of your repo should look like.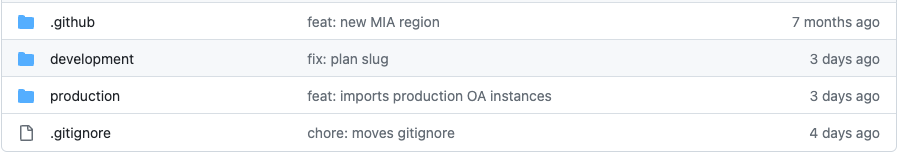
Variables
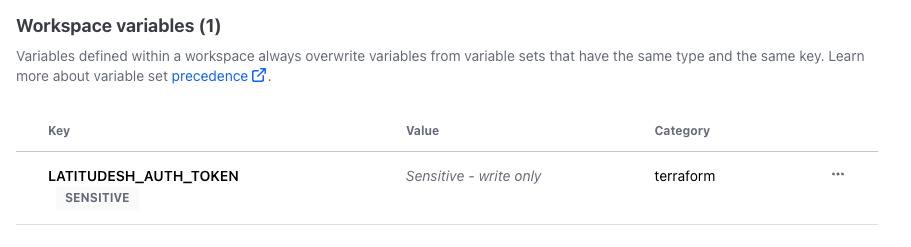
Select a workspace and go to Variables. Add a new sensitive variable namedLATITUDESH_AUTH_TOKEN with your Latitude.sh API Key as value.
Additional recommendations
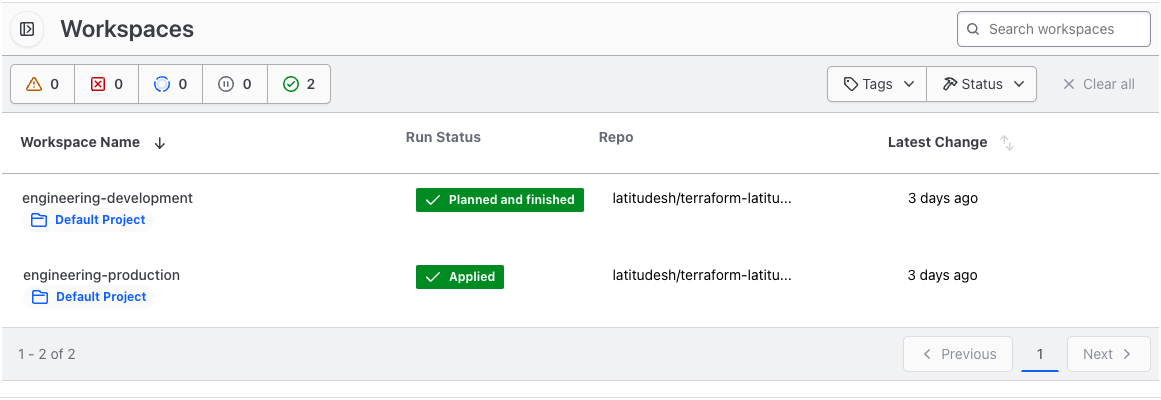
With this setup, whenever you push changes to themain branch
- Terraform Cloud will plan and apply your plan for the development workspace.
- Terraform Cloud will plan and wait for confirmation to apply your plan for the production workspace. You have to go to Terraform Cloud’s dashboard and approve the changes.
- Restrict repository access to developers working on your infrastructure.
- Create branch protection rules, the most important being protecting your
mainbranch.