Benefits & use cases
Private networking provides a myriad of benefits, with the most important ones being:- Traffic doesn’t go through the public internet, enhancing security.
- Private network traffic doesn’t count against your bandwidth quota.
- Connecting a database server to a web application privately.
- Managing internal services like DHCP.
- Setting up Kubernetes clusters with direct node communication.
Setup
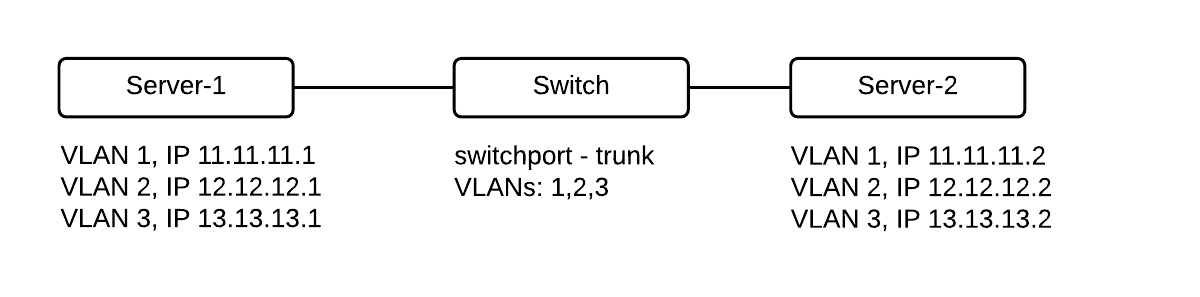
Step 1: Create a VLAN
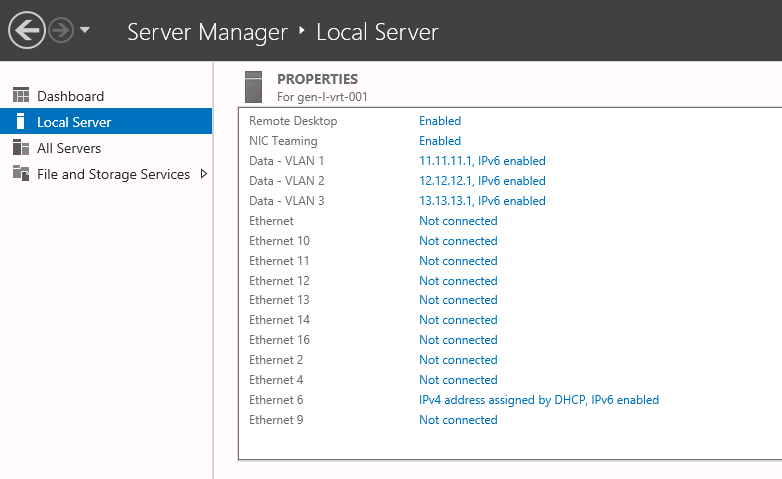
The first step is to create a Virtual Network — commonly referred to as VLAN.- From the dashboard
- Using the API
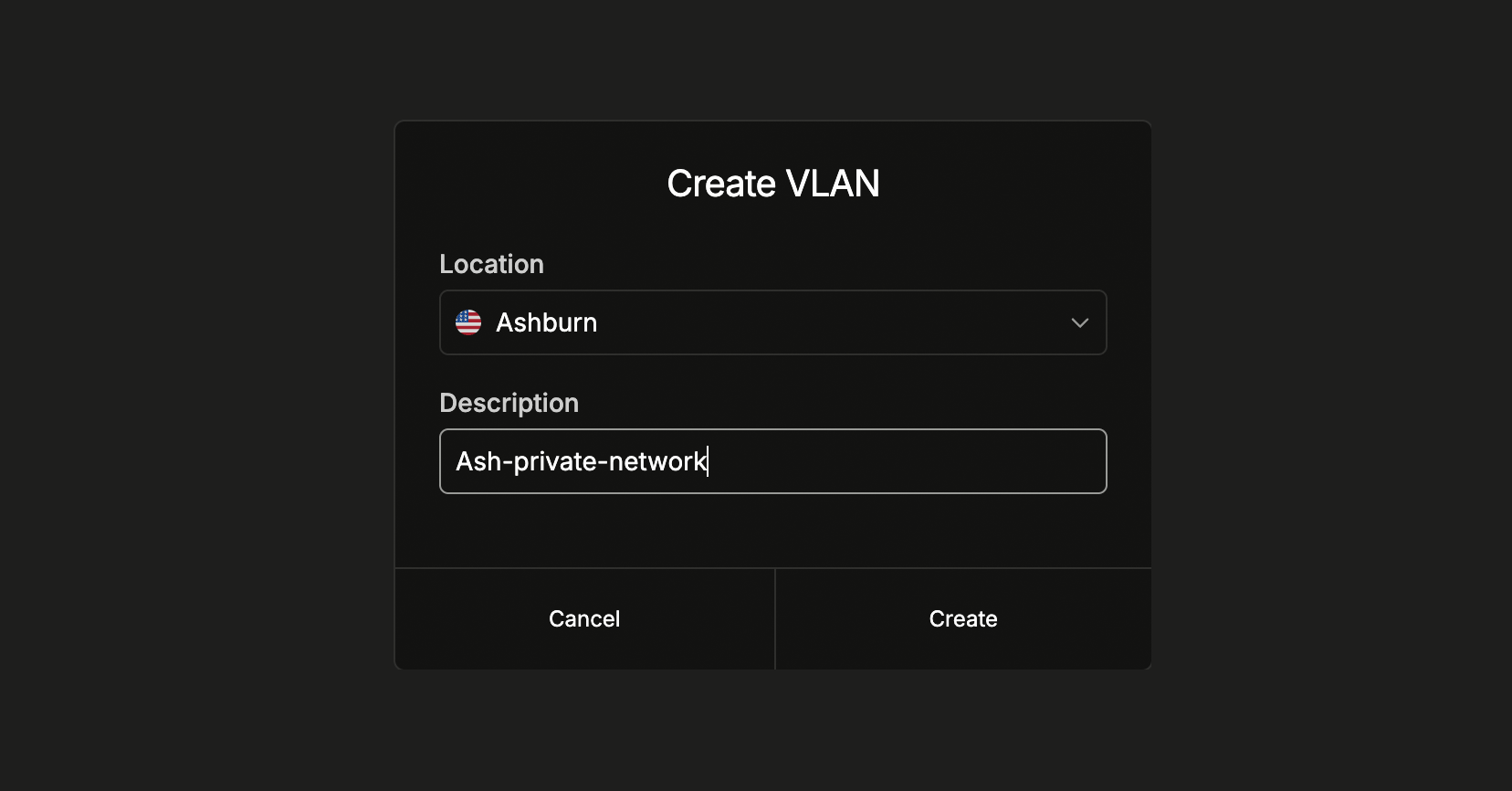
Create a VLAN
Log in to the dashboard, select a
project, navigate to Networking → Private networks in the sidebar menu,
and click Create VLAN. Select the location and add a description to help
you identify what the VLAN is used for.
Step 2: Assign servers
After creating the VLAN, assign at least two servers to allow the server’s private IPs to communicate.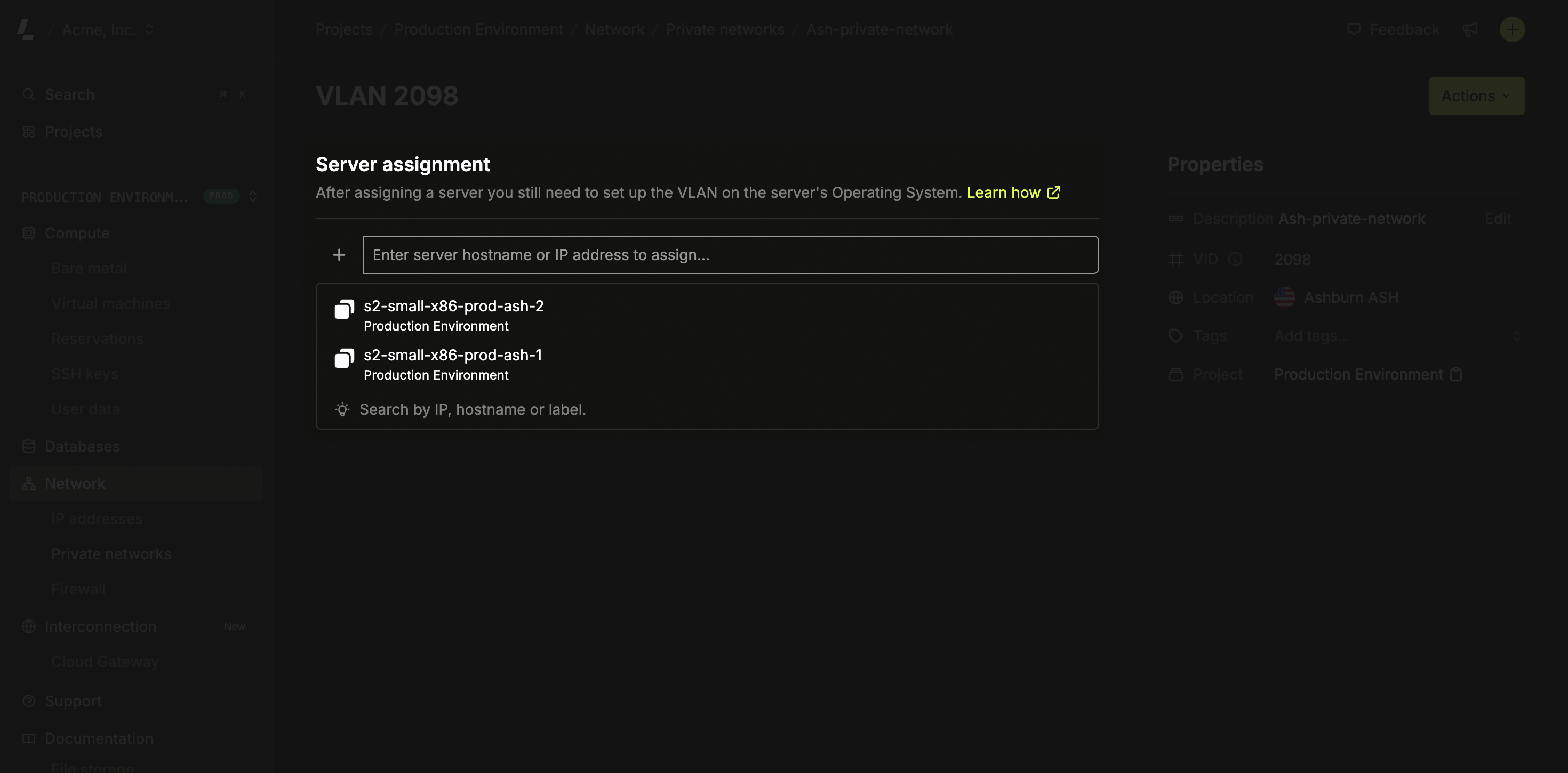
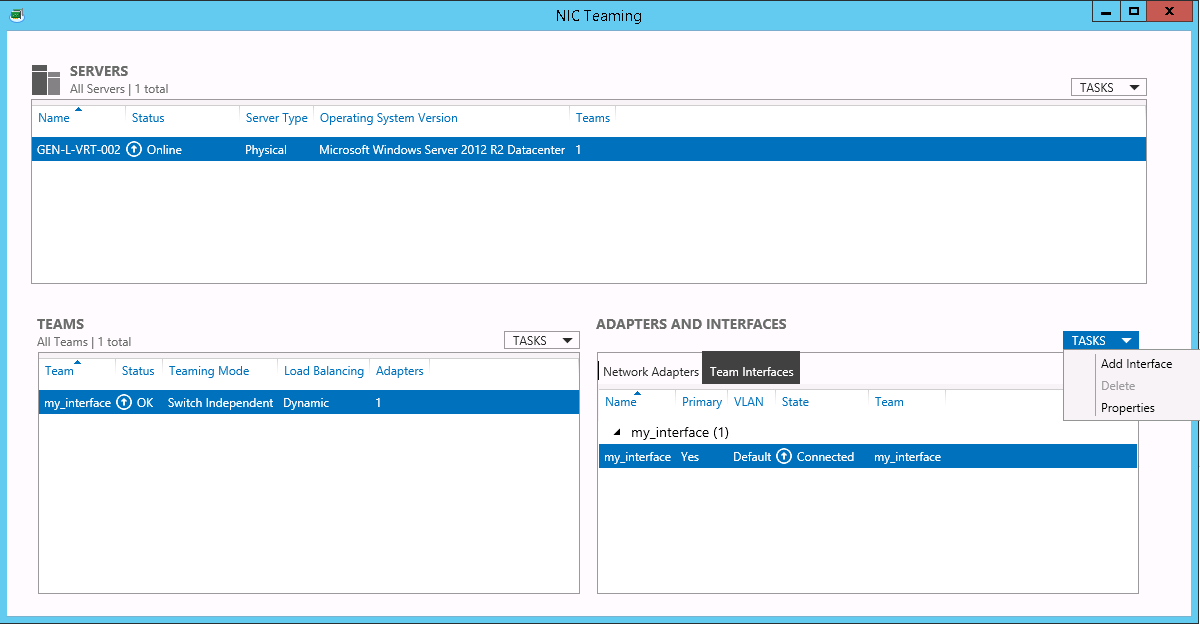
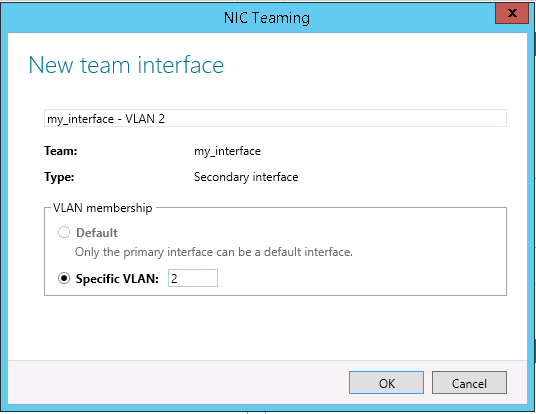
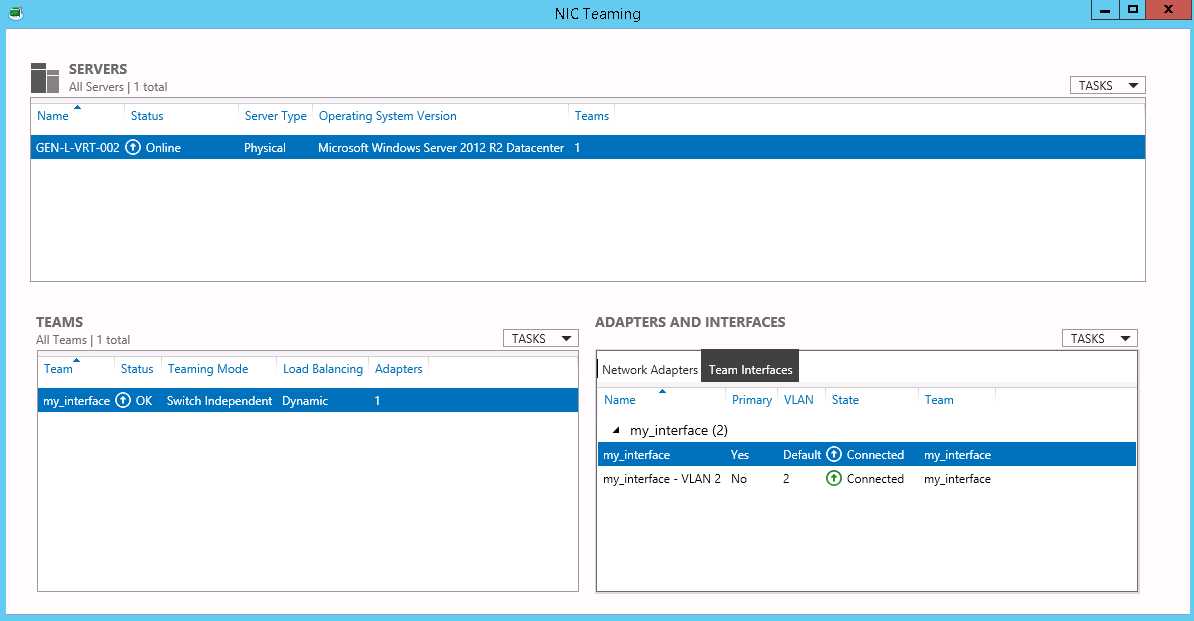
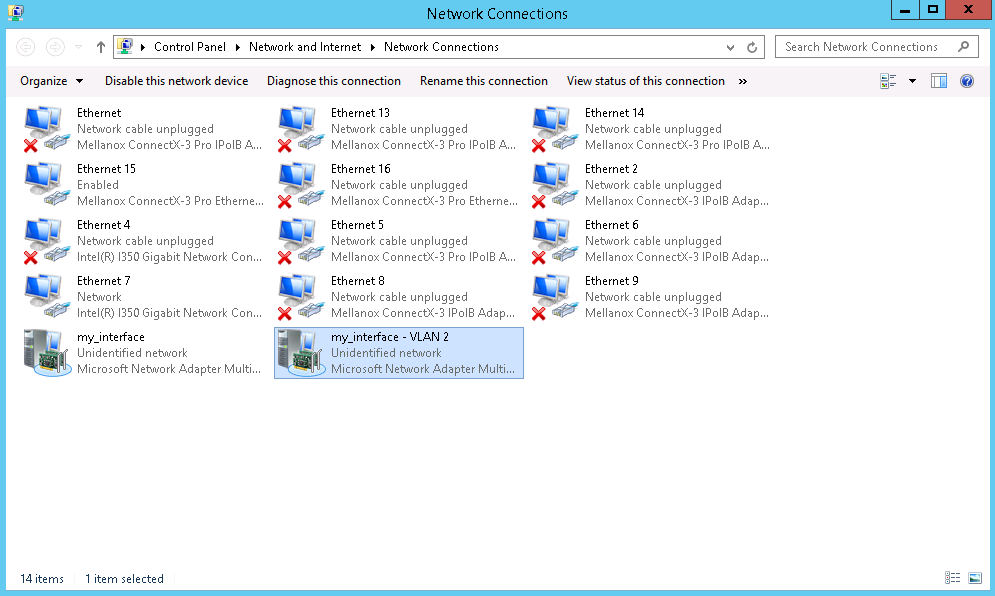
Step 3: Configure the OS
The network provisioning on Latitude.sh switches is handled automatically after you assign your first server to a VLAN. Latitude.sh has no access to your servers, an additional step is required, and you need to configure the VLAN on your Operating System.- Ubuntu
- Windows
- CentOS and RedHat Enterprise Linux
Change netplan
Change the Netplan configuration file in
/etc/netplan/50-cloud-init.yaml and add the configuration below to the end of the file.- Replace
{{VID}}with the VID value from the VLAN you created. - Replace
10.8.0.1with a private address of your choice. This address becomes the private IP of the server within the VLAN. It can be anything you want, but each server in the same VLAN needs a different IP. - Replace
eno2with the correct interface name. For servers with bonded interfaces, use bond0.
Adding a default route
Due to eventual changes in Netplan versions, to use Cloud Gateway, you need to define a default route to ensure proper network routing.
You can do that by adding the following routes section under the vlans key:
-
Replace
10.8.0.0/16with the network prefix you want to reach through eno2. -
Replace
192.168.0.1with the gateway IP address for your network (typically the first IP of your subnet).
Additional Resources
Setting up 802.1Q VLAN tagging using IFCFG files
Setting up 802.1Q VLAN tagging using IFCFG files
Configure the parent interface
Configure the parent interface in
/etc/sysconfig/network-scripts/ifcfg-eno2.Set the VLAN interface configuration
Set the VLAN interface configuration in the
/etc/sysconfig/network-scripts/ directory. The configuration file name should be the parent interface plus a . character followed by the VLAN ID number. For example, if the VLAN ID is 192, and the parent interface is eth0, then the configuration file name should be ifcfg-eno2.192:Set up the second VLAN
If there is a need to configure a second VLAN, with, for example, VLAN ID 193, on the same interface, eno2, add a new file with the name
eno2.193 with the VLAN configuration details. Restart the networking service in order for the changes to take effect. As root issue the following command: